Vulnerability Enrichment

We sometimes get asked how we enrich our vulnerability data, so we thought we would write a blog post that we can share when we get asked this question in the future.
Vulnerability Data
Our vulnerability data comes from the Common Vulnerabilities and Exposures (CVE) database, ran by MITRE (a non-profit, funded by the US government). We query the CVE data as it is released publicly, which is every hour, of every day. Parse the data and store it within our database.
This data sometimes, but not always, includes the following:
- Common Vulnerability Scoring System (CVSS) score
- Stakeholder-Specific Vulnerability Categorization (SSVC) data
- The affected product and vendor
- The affected versions
- Title, description and other details
When this data is not initially available from the CVE data, we update our database with any future CVE updates. As well as checking other trusted sources, such as the NIST National Vulnerability Database (NVD) for vulnerability updates.
Known Exploited
Knowing if a vulnerability is being exploited, or is likely to be exploited, is very valuable to vulnerability management teams to prioritise which vulnerabilities to focus on.
Exploit Prediction Scoring System (EPSS)
For the first 30 days of a vulnerabilities lifetime, we add and update the Exploit Prediction Scoring System (EPSS) data once per day. The EPSS, using machine learning, estimates the probability that a software vulnerability will be exploited in the wild. The higher the score, the more likely the vulnerability is to be exploited. The EPSS is not perfect at predicting exploitation, but it is just that, a "prediction", which can be used along with other data points to help make decisions. The EPSS is due for a big update, to version 4, on march 17th, 2025, which should make its predictions more accurate.
Stakeholder-Specific Vulnerability Categorization (SSVC)
The SSVC data, sometimes provided within CVE database data, indicates the state of exploitation of a vulnerability. If there's no exploitation, if a public PoC exists, or if there's evidence of active exploitation. It also includes the Technical Impact, and whether the exploit is Automatable. This data together, then allows users to decide whether to Track, Attend, or Act on the vulnerability.
Below are the possible values for the Active Exploitation field:

Source: https://www.cisa.gov/sites/default/files/publications/cisa-ssvc-guide%20508c.pdf
CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA, America's Cyber Defence Agency, maintains an authoritative source of vulnerabilities that have been exploited in the wild, named CISA KEV.
CyberAlerts monitors the CISA KEV catalog for any new entries every 10 minutes. When we detect a new entry, we update our database, and mark the vulnerability as being "known exploited".
News Articles / Vendor Advisories / Vulnerability Databases
We don't only monitor vulnerability data, but also "chatter" around the web, from sources such as TheHackerNews, Palo Alto Unit42, Japan Vulnerability Notes (JVN), Google Threat Intelligence and many other sources.
We parse the content of these news articles, matching the article to the vulnerabilities that they are discussing. For example, this article, titled Ivanti Flaw CVE-2025-0282 Actively Exploited, Impacts Connect Secure and Policy Secure, was linked to the CVE-2025-0282 vulnerability.
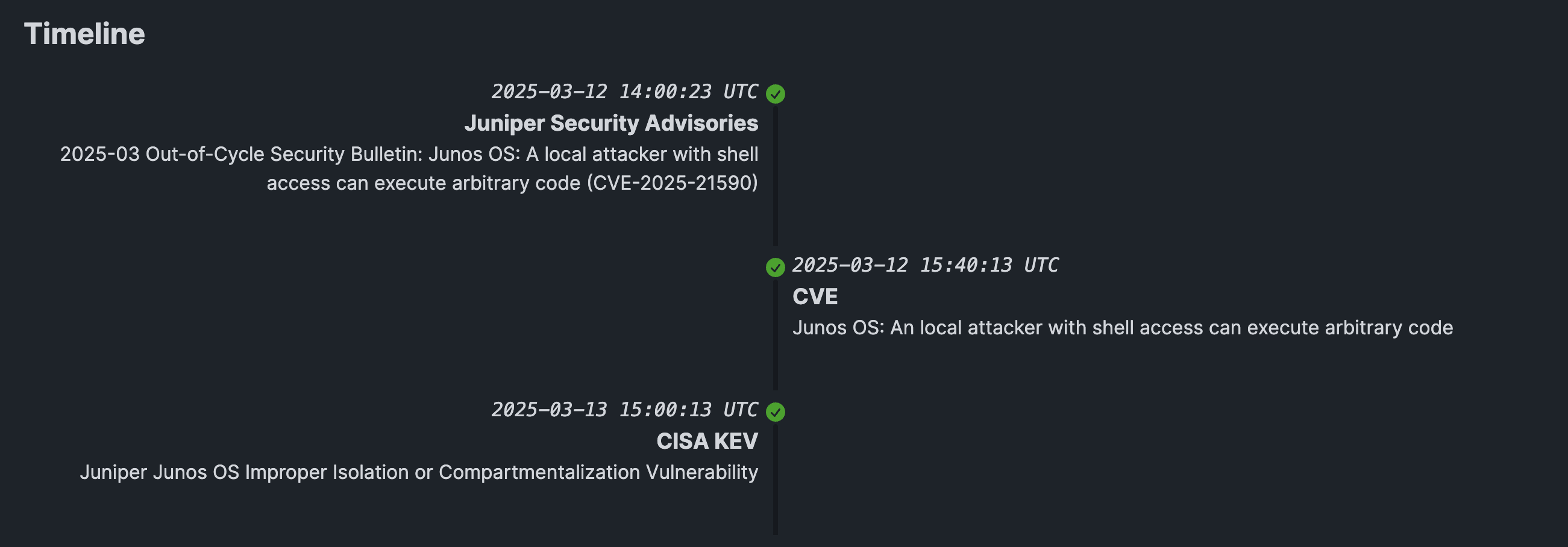
As well as linking the article to the vulnerability, we also look for exploitation clues in the article contents, do they mention that the vulnerability is being actively exploited?
Custom Filtering
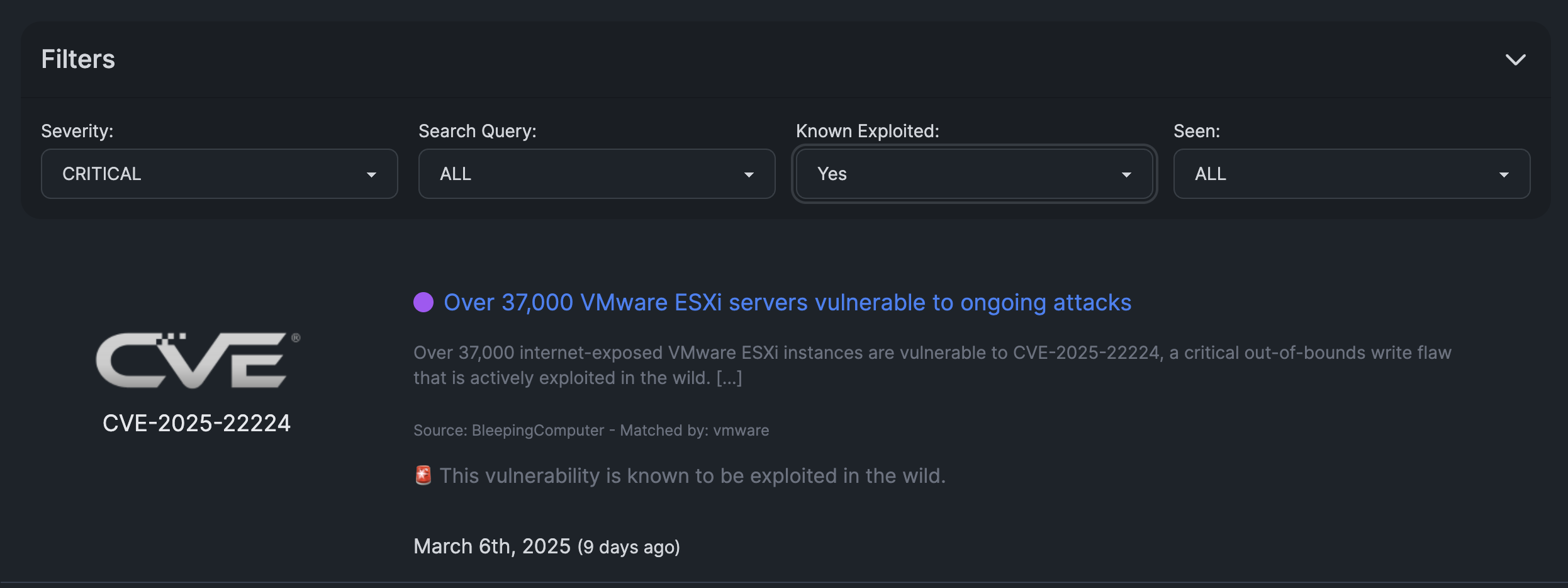
Once we store all this information in our database, it is continuously updated. CyberAlerts users can filter the vulnerabilities and articles by exact keywords, regular expressions, CVSS severity, known exploited and whether the user has already seen the vulnerability.
Alerting
CyberAlerts users can configure different alerting channels, such as email, custom RSS feeds, APIs and Slack to receive instant real-time alerts. The alerts use the user's filtering preferences so they are only alerted on what matters to their business; cutting out the noise.
Conclusion
We continually enrich our data with a variety of sources, that then allows our users to make critical decisions on how to prioritise vulnerabilities. We are always improving our vulnerability enrichment systems and adding more valuable data over time. Enrich baby.