How threat actors get their names

Ever wondered where threat actors got their names from? Names like the infamous Lazarus Group, APT42, Fancy Bear and others? Well, were here to find out!
The Lazarus Group, widely thought to be the nation state actor North Korea, first came on the radar of security professionals in 2009. Their first known campaigns were conducting Distributed Denial of Service (DDoS) attacks against South Korean and US websites. The group is also believed to be behind the infamous WannaCry ransomware attack in 2017. As well as a recent $1.5 Billion crypto heist of ByBit.
The "Lazarus Group" is not the only name attributed to this threat actor. They're also referred to as "Guardians of Peace", "Whois Team", "Hidden Cobra", "ZINC" "APT38" and "Dimond Street".
And rather less l33t sounding, it is believed that within North Korea itself, the groups is known as "414 Liaison Office".
But who assigns these fancy names?
The names largely come from Cyber Threat Intelligence (CTI) vendors, such as antivirus and other threat intelligence focused companies. Some of these companies include CrowdStrike, Kaspersky, Mandiant, and Microsoft.
These organisations will all assign names to threat actors differently; using their own naming conventions. They also assign different names to the same threat actors. Making it difficult for cyber security teams to keep track.
Here are some of the names given to the Lazarus Group by different organisations:
- Lazarus Group (Novetta/Kaspersky)
- Labyrinth Chollima (CrowdStrike)
- Diamond Sleet, fka ZINC (Microsoft)
- G0032 (MITRE ATT&CK)
- HIDDEN COBRA (CISA/US DHS)
- NICKEL ACADEMY (Secureworks)
- Guardians of Peace (self-given)
- New Romantic Cyber Army Team (McAfee)
- Whois Hacking Team (McAfee)
- Group 77 (Talos)
- Appleworm (origin unknown)
Source: https://eurepoc.eu/publication/apt-profile-lazarus-group/
CrowdStrike
CrowdStrike use animals in their naming convention, such as "Bear" for Russian nation state threat actors. "Kitten" for Iran. "Chollima" for North Korea. Or "Spider" for cybercrime.
Mandiant
Mandiant, now owned by Google, were the first to use the APT[integer] naming convention, by attributing APT1 to the Chinese Government in 2013. Although the term itself, "advanced persistent threat", is cited as originating in the United States Air Force in 2006. Mandiant uses the "UNC" naming convention for uncategorized groups. But will also use "APT" and "FIN" groups.
Microsoft
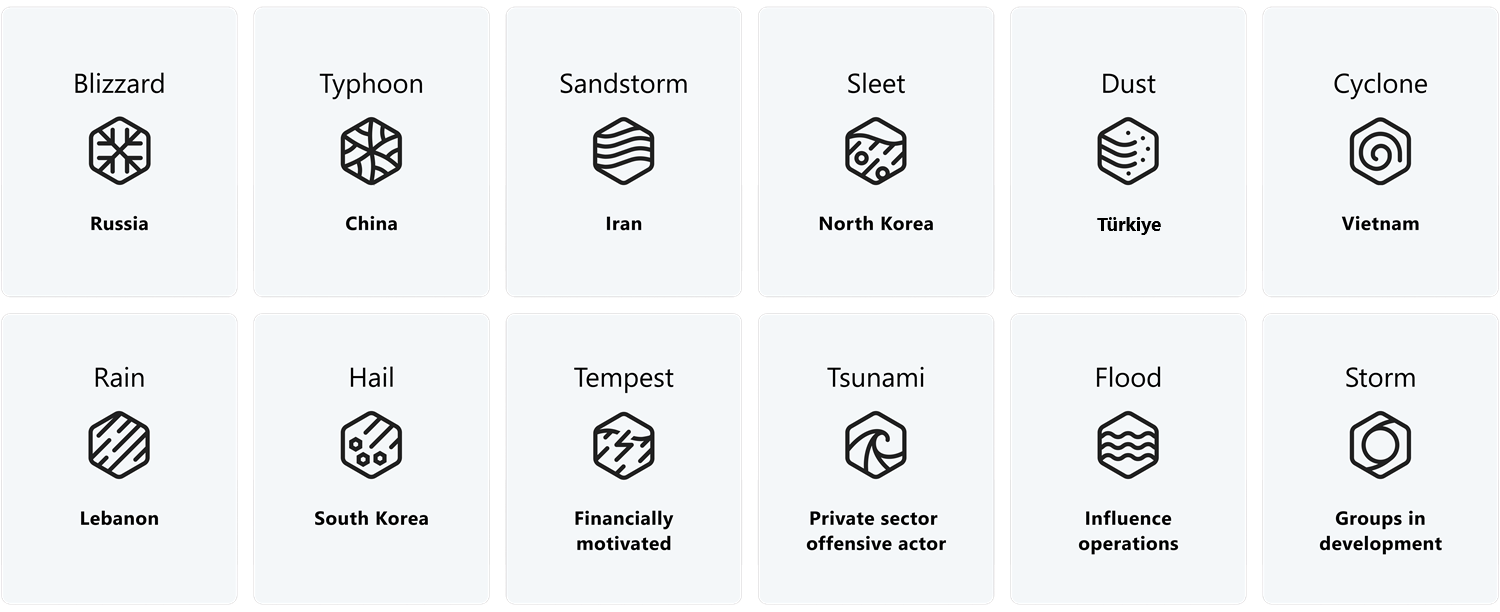
Microsoft used to use the periodic table for naming threat actors. I guess they ran out of elements? But since 2023, they now use... weather events?!
Conclusion
It would be difficult for all organisations to agree on a name for threat actors, as attribution is hard and messy, and usually takes a lot of time to do right. So anyone can name any threat actor what they like, using their own naming conventions. The names are usually first used by companies investigating APTs and then widely used by the cyber security community.
"There is no ultimate arbiter of APT naming conventions" - https://www.cisa.gov/topics/cyber-threats-and-advisories/nation-state-cyber-actors
There are, however, some threat actor lists that are regularly updated by various trusted organisations; one being the MITRE ATT&ACK Groups, and Google Cloud's APT page.
And here comes the obligatory plug. If you want to track any of these threat actors, CyberAlerts can help you do so by creating a search query with the threat actor's name. Below is a screenshot of someone (me) monitoring the "Russia" keyword:
Microsoft Publicly Disclosed Threat Actor Names
The following table lists Microsoft's publicly disclosed threat actor names from March 14th, 2025, with their origin or threat actor category, previous names, and corresponding names used by other security vendors where available.
| Threat actor name | Origin/Threat actor category | Other names |
|---|---|---|
| Amethyst Rain | Lebanon | Volatile Cedar |
| Antique Typhoon | China | Storm-0558 |
| Aqua Blizzard | Russia | ACTINIUM, Gamaredon, Armageddon, UNC530, shuckworm, SectorC08, Primitive Bear |
| Blue Tsunami | Israel, Private sector offensive actor | |
| Brass Typhoon | China | BARIUM, APT41 |
| Brocade Typhoon | China | BORON, UPS, Gothic Panda, APT3, OLDCARP, TG-0110, Red Sylvan, CYBRAN |
| Burgundy Sandstorm | Iran | Cadelle, Chafer |
| Cadet Blizzard | Russia | DEV-0586 |
| Canary Typhoon | China | CIRCUIT PANDA, APT24, Palmerworm, BlackTech |
| Canvas Cyclone | Vietnam | BISMUTH, OceanLotus, APT32 |
| Caramel Tsunami | Israel, Private sector offensive actor | DEV-0236 |
| Carmine Tsunami | Private sector offensive actor | |
| Charcoal Typhoon | China | CHROMIUM, ControlX, Aquatic Panda, RedHotel, BRONZE UNIVERSITY |
| Checkered Typhoon | China | CHLORINE, ATG50, APT19, TG-3551, DEEP PANDA, Red Gargoyle |
| Cinnamon Tempest | China, Financially motivated | DEV-0401 |
| Circle Typhoon | China | DEV-0322, APT6, APT27 |
| Citrine Sleet | North Korea | DEV-0139, Storm-0139, Storm-1222, DEV-1222 |
| Cotton Sandstorm | Iran | NEPTUNIUM, Vice Leaker, Haywire Kitten |
| Crescent Typhoon | China | CESIUM |
| Crimson Sandstorm | Iran | CURIUM, Tortoise Shell, HOUSEBLEND, TA456 |
| Cuboid Sandstorm | Iran | DEV-0228 |
| Denim Tsunami | Austria, Private sector offensive actor | DEV-0291 |
| Diamond Sleet | North Korea | ZINC, Black Artemis, Labyrinth Chollima, Lazarus |
| Emerald Sleet | North Korea | THALLIUM, RGB-D5, Black Banshee, Kimsuky, Greendinosa, VELVET CHOLLIMA |
| Fallow Squall | Singapore | PLATINUM, PARASITE, RUBYVINE, GINGERSNAP |
| Flax Typhoon | China | Storm-0919, ETHEREAL PANDA |
| Forest Blizzard | Russia | STRONTIUM, Sednit, ATG2, Sofacy, FANCY BEAR, Blue Athena, Z-Lom Team, Operation Pawn Storm, Tsar Team, CrisisFour, HELLFIRE, APT28 |
| Ghost Blizzard | Russia | BROMINE, TG-4192, Koala Team, ENERGETIC BEAR, Blue Kraken, Crouching Yeti, Dragonfly |
| Gingham Typhoon | China | GADOLINIUM, TEMP.Periscope, Leviathan, JJDoor, APT40, Feverdream |
| Granite Typhoon | China | GALLIUM |
| Gray Sandstorm | Iran | DEV-0343 |
| Hazel Sandstorm | Iran | EUROPIUM, COLBALT GYPSY, Crambus, OilRig, APT34 |
| Heart Typhoon | China | HELIUM, APT17, Hidden Lynx, ATG3, Red Typhon, KAOS, TG-8153, SportsFans, DeputyDog, AURORA PANDA, Tailgater |
| Hexagon Typhoon | China | HYDROGEN, Calc Team, Red Anubis, APT12, DNS-Calc, HORDE, NUMBERED PANDA |
| Houndstooth Typhoon | China | HASSIUM, isoon, deepclif |
| Jade Sleet | North Korea | Storm-0954 |
| Lace Tempest | Financially motivated | DEV-0950 |
| Lemon Sandstorm | Iran | RUBIDIUM |
| Leopard Typhoon | China | LEAD, TG-2633, TG-3279, Mana, KAOS, Red Diablo, Winnti Group |
| Lilac Typhoon | China | DEV-0234 |
| Linen Typhoon | China | IODINE, Red Phoenix, Hippo, Lucky Mouse, EMISSARY PANDA, BOWSER, APT27, Wekby2, UNC215, TG-3390 |
| Luna Tempest | Financially motivated | |
| Magenta Dust | Türkiye | PROMETHIUM, StrongPity, SmallPity |
| Manatee Tempest | Russia | |
| Mango Sandstorm | Iran | MERCURY, SeedWorm, STATIC KITTEN, TEMP.Zagros, MuddyWater |
| Marbled Dust | Türkiye | SILICON, Sea Turtle, UNC1326 |
| Marigold Sandstorm | Iran | DEV-500 |
| Midnight Blizzard | Russia | NOBELIUM, UNC2452, APT29, Cozy Bear |
| Mint Sandstorm | Iran | PHOSPHORUS, Parastoo, Newscaster, APT35, Charming Kitten |
| Moonstone Sleet | North Korea | Storm-1789 |
| Mulberry Typhoon | China | MANGANESE, Backdoor-DPD, COVENANT, CYSERVICE, Bottle, Red Horus, Red Naga, Auriga, KEYHOLE PANDA, APT5, ATG48, TG-2754, tabcteng |
| Mustard Tempest | Financially motivated | DEV-0206 |
| Night Tsunami | Israel | DEV-0336 |
| Nylon Typhoon | China | NICKEL, Playful Dragon, RedRiver, ke3chang, VIXEN PANDA, APT15, Mirage |
| Octo Tempest | Financially motivated | 0ktapus, Scattered Spider |
| Onyx Sleet | North Korea | PLUTONIUM, StoneFly, Tdrop2 campaign, DarkSeoul, Black Chollima, SILENT CHOLLIMA, Andariel, APT45 |
| Opal Sleet | North Korea | OSMIUM, Planedown, Konni, APT43 |
| Peach Sandstorm | Iran | HOLMIUM, APT33, Elfin, REFINED KITTEN |
| Pearl Sleet | North Korea | LAWRENCIUM |
| Periwinkle Tempest | Russia | DEV-0193 |
| Phlox Tempest | Israel, Financially motivated | DEV-0796 |
| Pink Sandstorm | Iran | AMERICIUM, Agrius, Deadwood, BlackShadow, SharpBoys, FireAnt, Justice Blade |
| Pinstripe Lightning | NIOBIUM, Desert Falcons, Scimitar, Arid Viper | |
| Pistachio Tempest | Financially motivated | DEV-0237 |
| Plaid Rain | Lebanon | POLONIUM |
| Pumpkin Sandstorm | Iran | DEV-0146 |
| Purple Typhoon | China | POTASSIUM, GOLEM, Evilgrab, AEON, LIVESAFE, ChChes, APT10, Haymaker, Webmonder, STONE PANDA, Foxtrot, Foxmail, MenuPass, Red Apollo |
| Raspberry Typhoon | China | RADIUM, LotusBlossom, APT30 |
| Ruby Sleet | North Korea | CERIUM |
| Ruza Flood | Russia, Influence operations | |
| Salmon Typhoon | China | SODIUM, APT4, MAVERICK PANDA |
| Salt Typhoon | China | GhostEmperor, FamousSparrow |
| Sangria Tempest | Ukraine, Financially motivated | ELBRUS |
| Sapphire Sleet | North Korea | COPERNICIUM, Genie Spider, BlueNoroff, CageyChameleon, CryptoCore |
| Satin Typhoon | China | SCANDIUM, COMBINE, TG-0416, SILVERVIPER, DYNAMITE PANDA, Red Wraith, APT18, Elderwood Group, Wekby |
| Seashell Blizzard | Russia | IRIDIUM, BE2, UAC-0113, Blue Echidna, Sandworm, PHANTOM, BlackEnergy Lite, APT44 |
| Secret Blizzard | Russia | KRYPTON, VENOMOUS BEAR, Uroburos, Snake, Blue Python, Turla, WRAITH, ATG26 |
| Sefid Flood | Iran, Influence operations | |
| Shadow Typhoon | China | DarkShadow, Oro0lxy |
| Silk Typhoon | China | HAFNIUM, timmy |
| Smoke Sandstorm | Iran | UNC1549 |
| Spandex Tempest | Financially motivated | TA505 |
| Spotted Sandstorm | NEODYMIUM, BlackOasis | |
| Star Blizzard | Russia | SEABORGIUM, COLDRIVER, Callisto Group, BlueCharlie, TA446 |
| Storm-0216 | Financially motivated | Twisted Spider, UNC2198 |
| Storm-0230 | Group in development | Conti Team 1, DEV-0230 |
| Storm-0247 | China | ToddyCat, Websiic |
| Storm-0288 | Group in development | FIN8 |
| Storm-0302 | Group in development | Narwhal Spider, TA544 |
| Storm-0501 | Financially motivated | DEV-0501 |
| Storm-0538 | Group in development | FIN6 |
| Storm-0539 | Financially motivated | |
| Storm-0569 | Financially motivated | DEV-0569 |
| Storm-0671 | Group in development | UNC2596, Tropicalscorpius |
| Storm-0940 | China | |
| Storm-0978 | Russia | RomCom, Underground Team |
| Storm-1101 | Group in development | |
| Storm-1113 | Financially motivated | |
| Storm-1152 | Financially motivated | |
| Storm-1175 | China, Financially motivated | |
| Storm-1194 | Group in development | MONTI |
| Storm-1516 | Russia, Influence operations | |
| Storm-1567 | Financially motivated | |
| Storm-1674 | Financially motivated | |
| Storm-1679 | Influence operations | |
| Storm-1811 | Financially motivated | |
| Storm-1982 | China | SneakyCheff, UNK_SweetSpecter |
| Storm-2035 | Iran, Influence operations | |
| Storm-2077 | China | TAG-100 |
| Strawberry Tempest | Financially motivated | DEV-0537, LAPSUS$ |
| Sunglow Blizzard | DEV-0665 | |
| Swirl Typhoon | China | TELLURIUM, Tick, Bronze Butler, REDBALDKNIGHT |
| Taffeta Typhoon | China | TECHNETIUM, TG-0055, Red Kobold, JerseyMikes, APT26, BEARCLAW |
| Taizi Flood | China, Influence operations | Dragonbridge, Spamouflage |
| Tumbleweed Typhoon | China | THORIUM, Karst |
| Twill Typhoon | China | TANTALUM, BRONZE PRESIDENT, LuminousMoth, MUSTANG PANDA |
| Vanilla Tempest | Financially motivated | DEV-0832, Vice Society |
| Velvet Tempest | Financially motivated | DEV-0504 |
| Violet Typhoon | China | ZIRCONIUM, Chameleon, APT31, WebFans |
| Volga Flood | Russia, Influence operations | Storm-1841, Rybar |
| Volt Typhoon | China | BRONZE SILHOUETTE, VANGUARD PANDA |
| Wheat Tempest | Financially motivated | GOLD, Gatak |
| Wisteria Tsunami | India, Private sector offensive actor | DEV-0605 |
| Zigzag Hail | Korea | DUBNIUM, Nemim, TEMPLAR, TieOnJoe, Fallout Team, Purple Pygmy, Dark Hotel, Egobot, Tapaoux, PALADIN, Darkhotel |
Source: https://learn.microsoft.com/en-gb/unified-secops-platform/microsoft-threat-actor-naming